Unveiling the Power of Kill Disk
In the labyrinthine world of digital information, safeguarding sensitive data from unauthorized access has become paramount. Kill disk emerges as an indispensable tool that empowers users to eradicate data permanently, leaving no trace behind. Whether it’s decommissioning old devices, ensuring privacy during device disposal, or thwarting forensic recovery attempts, kill disk offers an unparalleled level of data obliteration.

Image: www.youtube.com
What is Kill Disk?
Kill disk is a software utility or hardware device that is specifically designed to overwrite and sanitize storage media, rendering data irretrievable even by advanced forensic techniques. Unlike conventional deletion methods that simply mark files as “missing,” kill disk employs sophisticated algorithms to overwrite every sector of the storage device with random patterns of data. This process ensures that the original data is permanently destroyed and cannot be reconstructed.
How to Use Kill Disk Effectively
-
Choosing a Kill Disk Method
The choice of kill disk method depends on the specific device and data protection requirements. Software-based kill disk utilities offer ease of use and can be applied to a wide range of devices, including hard drives, SSDs, and USB drives. Hardware-based kill disk devices, on the other hand, provide enhanced security and are particularly suitable for highly sensitive data and military applications.
-
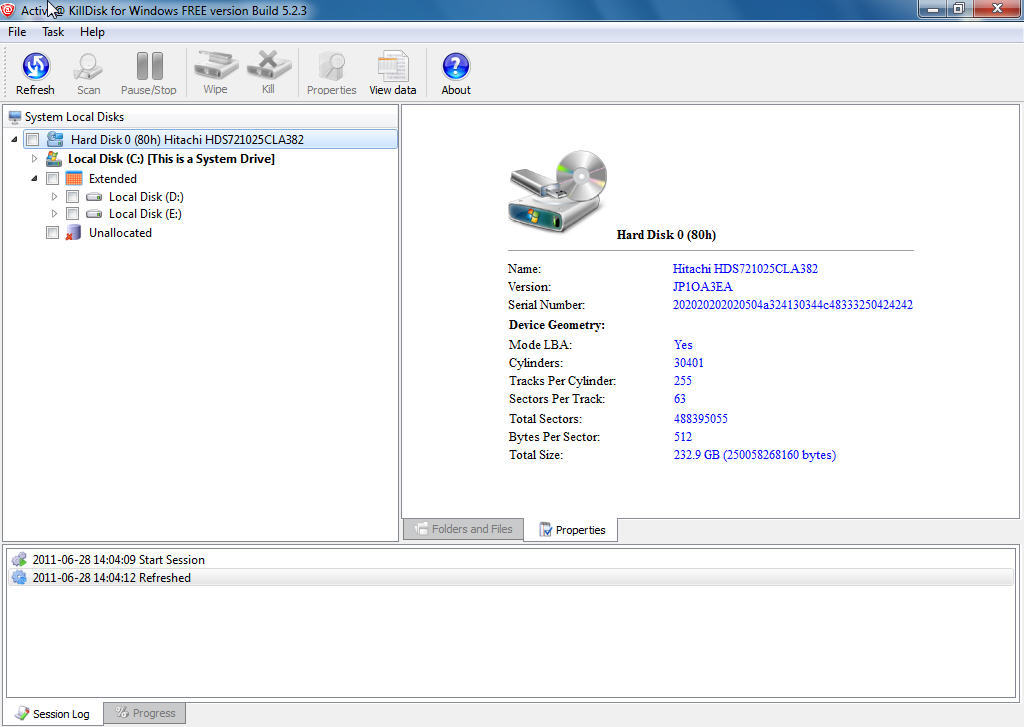
Image: softdeluxe.comPreparing the Storage Device
Before proceeding with kill disk, it’s crucial to ensure that you have backed up all essential data, as the process is irreversible. Disconnect the device from any networks or external devices to avoid potential interruptions.
-
Initiating the Kill Disk Process
Once the preparatory steps are complete, launch the kill disk software or activate the hardware device. The process typically involves selecting the appropriate overwriting algorithm, which determines the number of passes required to overwrite the storage medium. Common algorithms include DoD 5220.22-M, NIST 800-88 Revision 1, and Gutmann Method.
-
Verification and Validation
After the kill disk process is completed, it’s essential to verify the successful erasure of data. Most kill disk utilities provide built-in verification tools that scan the storage device to ensure that every sector has been overwritten. Additionally, third-party data recovery tools can be used to attempt recovery, confirming the effectiveness of the kill disk process.
Expert Tips and Considerations
-
Choosing the Right Algorithm
The choice of overwriting algorithm is an important decision that affects the level of data protection. Single-pass algorithms provide basic data sanitization, while multi-pass algorithms offer enhanced security. The DoD 5220.22-M standard recommends a minimum of three overwrites for magnetic media and seven overwrites for solid-state drives.
-
Physical vs. Logical Sanitization
Kill disk software performs logical sanitization by overwriting data at the file system level, while hardware-based kill disk devices employ physical sanitization that overwrites the storage medium at a hardware level. Both methods can effectively destroy data, but hardware-based sanitization is generally considered more secure.
FAQs on Kill Disk
-
What are the advantages of using kill disk?
Kill disk provides permanent and irreversible data erasure, ensuring privacy protection and preventing sensitive data from falling into the wrong hands.
-
How To Use Kill Disk
Is kill disk necessary for everyday use?
While kill disk is not essential for everyday deletion of files, it is highly recommended for disposing of devices containing sensitive information or when compliance with data protection regulations is required.